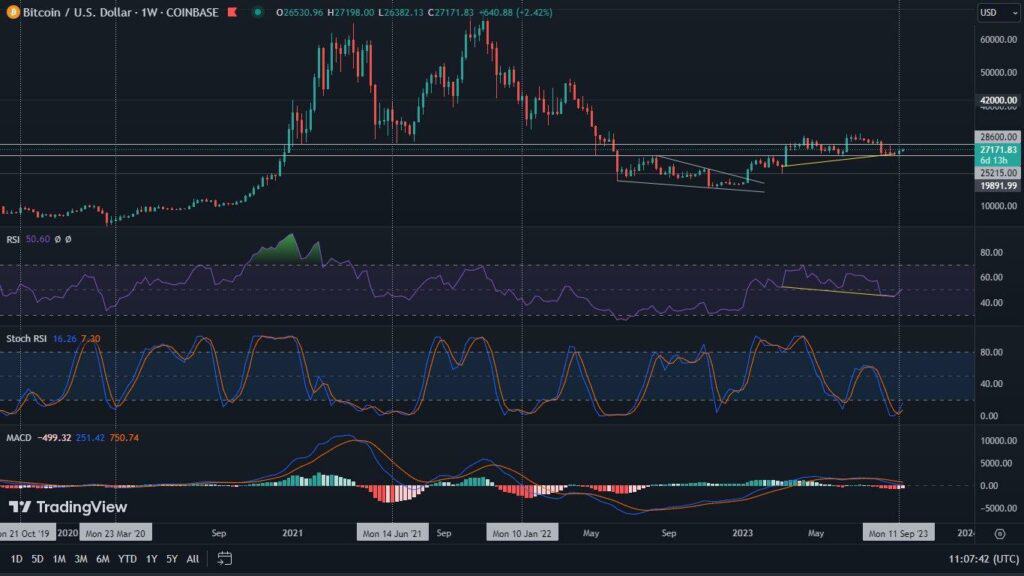
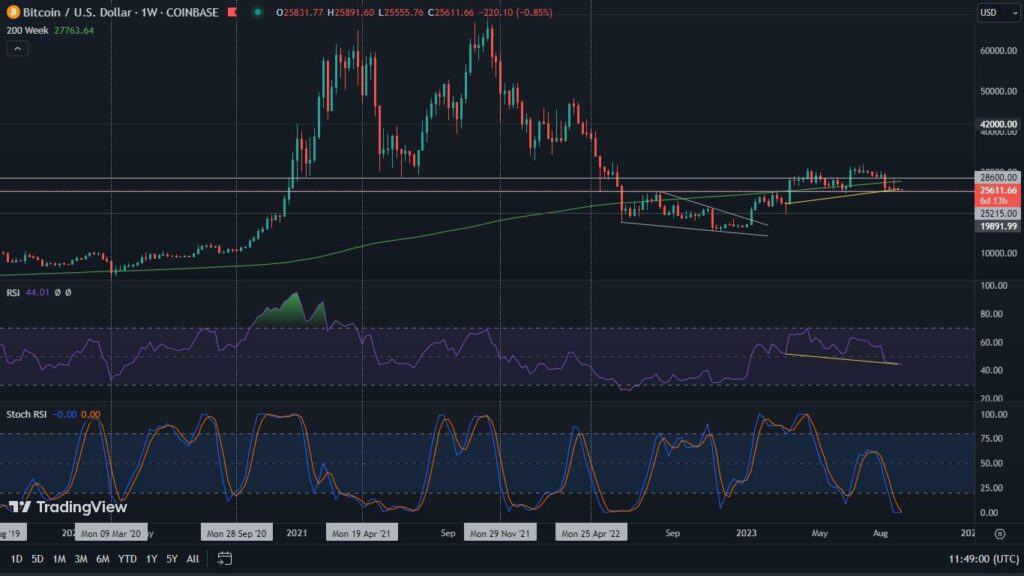
There are several methods available in blockchain for securing networks and verifying transactions. The two most popular are consensus algorithms based on Proof of Work (POW) and Proof of Stake (POS). With these, you can also earn new coins. In this article, we’ll tell you how they work.
The two biggest consensus algorithms – how they work
Proof of Work, is the first and most well-known cryptographic algorithm. It is on the basis of which the Bitcoin network functions. It would seem, therefore, that it was created with the emergence of the king of cryptocurrencies. Nothing could be further from the truth.
Proof of Work (POW)
The origins of POW date back to 1997, when Adam Back introduced its seeds in the form of Hashcash. The Hashcash system was initially designed to eliminate spam in email correspondence by forcing web users to perform simple mathematical operations. It turned out that after a few years exactly the same methodology was implemented by Satoshi Nakamoto for Bitcoin mining. Miners thus have to solve mathematical operations by which they acquire the cryptocurrency. The vast majority of crypto projects use a similar solution. An important element of the system is that it requires work to be done, which makes cryptocurrencies based on this consensus quite trusted. Moreover, the POW algorithm prevents the so-called double spending, i.e. spending the same funds twice. Thanks to the fact that the blockchain is public and all transactions can be tracked, we know that the same coin was not spent twice.
Proof of Stake (POS)
The Proof of Stake, on the other hand, works in a slightly different way. In this consensus the work of coin mining is abandoned. In its place appears the so-called proof of stake. This consists in the fact that validators are selected to operate the network. On a voluntary basis, anyone can become one, thus securing their funds as a deposit. The higher the deposit, the higher the probability that the algorithm will choose this particular node as the controller, creator and sender of the next block. The POS concept was presented for the first time in 2011 and it was aimed at solving the problems occurring in POW. It is worth noting on this occasion that today the eyes of the blockchain world are on Ethereum and its process of transitioning from the POW algorithm to POS. When this happens, the Ethereum network will most likely be the largest one running on staking.
Advantages and disadvantages of Proof of Work and Proof of Stake
Both of the algorithms presented are considered secure and functional. However, the differences are significant. First of all, the POW algorithm is based on very high energy expenditure. This is perfectly demonstrated by Bitcoin itself, which initially could be mined on any computer. Today, on the other hand, it requires a robust infrastructure to perform complex calculations, which involves significant power consumption. This is undoubtedly a negative element, but it has a positive side. It lets us know that there is value behind acquiring Bitcoin, and that it did not come out of nowhere.
Meanwhile, POS is a security in itself. With deposits, the network defends itself against breaches of its rules and when the algorithm encounters attempts to falsify the code, by at least attempting to double-spend the funds, it can easily block the validator by taking back the assets they have deposited. This is an excellent solution to prevent fraud. In addition, and very importantly, the energy consumption of using a POS is almost negligible and therefore much greener.